Cross-Origin Resource Sharing (CORS)
Overview
The CORS (Cross-Origin Resource Sharing) Policy controls how resources on a server can be accessed from different origins. It is crucial for web applications that rely on APIs hosted on different domains. The CORS policy ensures secure cross-origin requests by defining allowed methods, headers, credentials, and caching behavior.
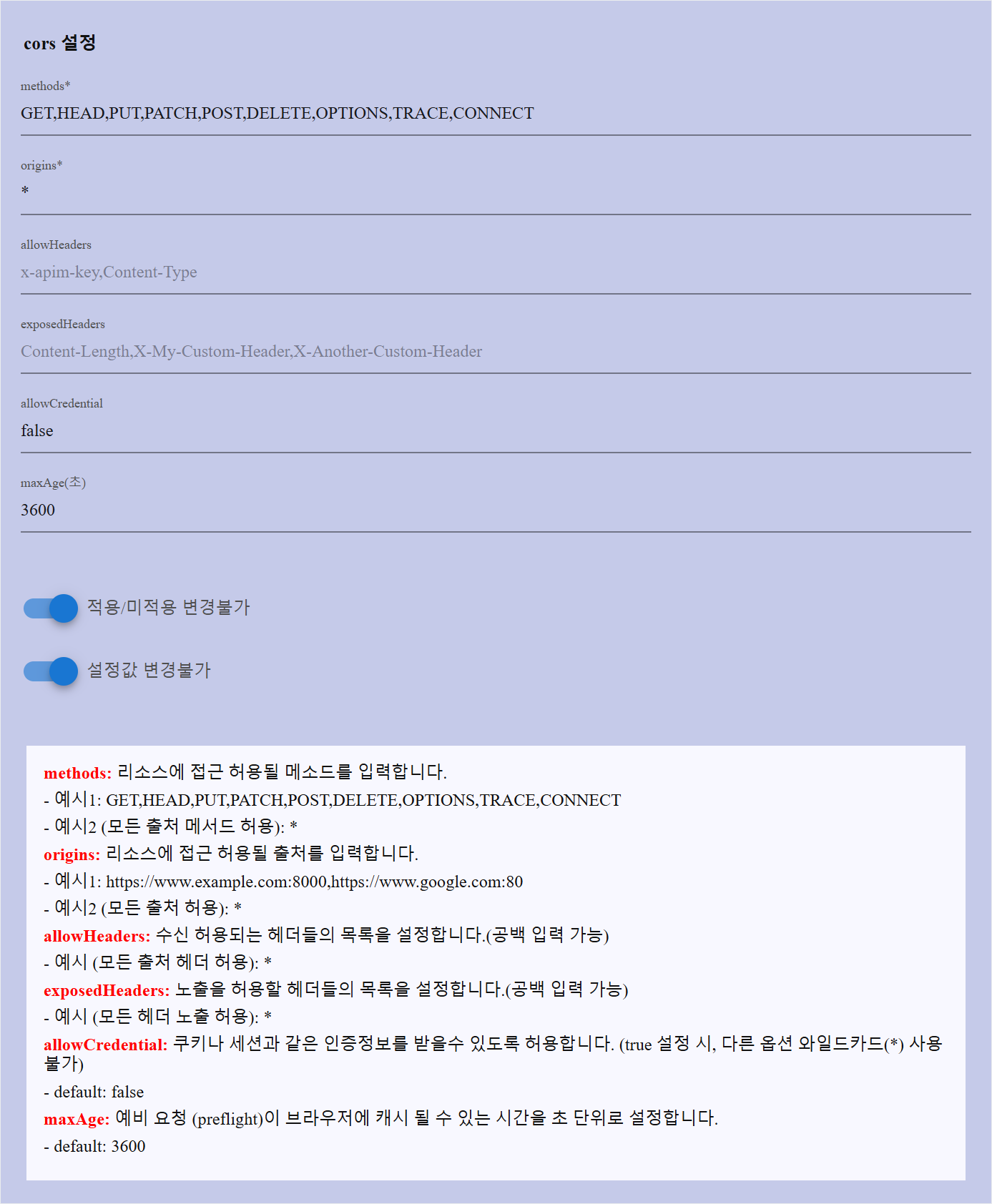
Configuration Details
The CORS Policy includes several key settings that control access and security:
| Field | Description | Example Values | Notes |
|---|---|---|---|
| methods | Defines allowed HTTP methods. | GET, HEAD, PUT, PATCH, POST, DELETE, OPTIONS, TRACE, CONNECT | Use * to allow all methods. |
| origins | Specifies the allowed origins (domains). | https://www.example.com:8000, https://www.google.com:80 | Use * to allow all origins. |
| allowHeaders | Lists the allowed request headers. | x-apim-key, Content-Type | Use * to allow all headers. |
| exposedHeaders | Defines headers that should be exposed to the client. | Content-Length, X-My-Custom-Header, X-Another-Custom-Header | Use * to expose all headers. |
| allowCredential | Determines if credentials (cookies, authentication) are allowed. | true / false | If true, * cannot be used in origins or allowHeaders. Default: false. |
| maxAge | Duration (in seconds) that the preflight request is cached. | 3600 | Default: 3600 (1 hour). |
Note:
- Avoid using in origins unless necessary to prevent security risks.
- Set allowCredential to false if authentication credentials are not required.
- Only expose necessary headers in exposedHeaders.
- Increase maxAge to reduce unnecessary preflight requests.
- Limit the allowed methods and headers to only what is needed.