SAML
Overview
SAML (Security Assertion Markup Language) is an open standard that facilitates authentication and authorization between different parties. It is commonly used in Single Sign-On (SSO) systems, allowing users to log in once and gain access to multiple services without re-entering their credentials.
SAML Plugin in the Kong API Gateway
The SAML specification defines three key roles:
- Principal – The user who logs in.
- Identity Provider (IdP) – The entity that authenticates users and issues identity assertions.
- Service Provider (SP) – The application or system that receives authentication assertions.
In the Kong API Gateway, the SAML plugin acts as the Service Provider (SP) and is responsible for initiating a login to the IdP (SP-initiated login).
Key Features of the SAML Plugin
- SSO Implementation: Redirects unauthenticated users to the IdP’s login page and, upon authentication, grants access to protected services.
- Session Management: Maintains user sessions using cookies for tracking session states.
- Form Handling: Supports IdP authentication flow via POST requests, ensuring the security of authentication parameters.
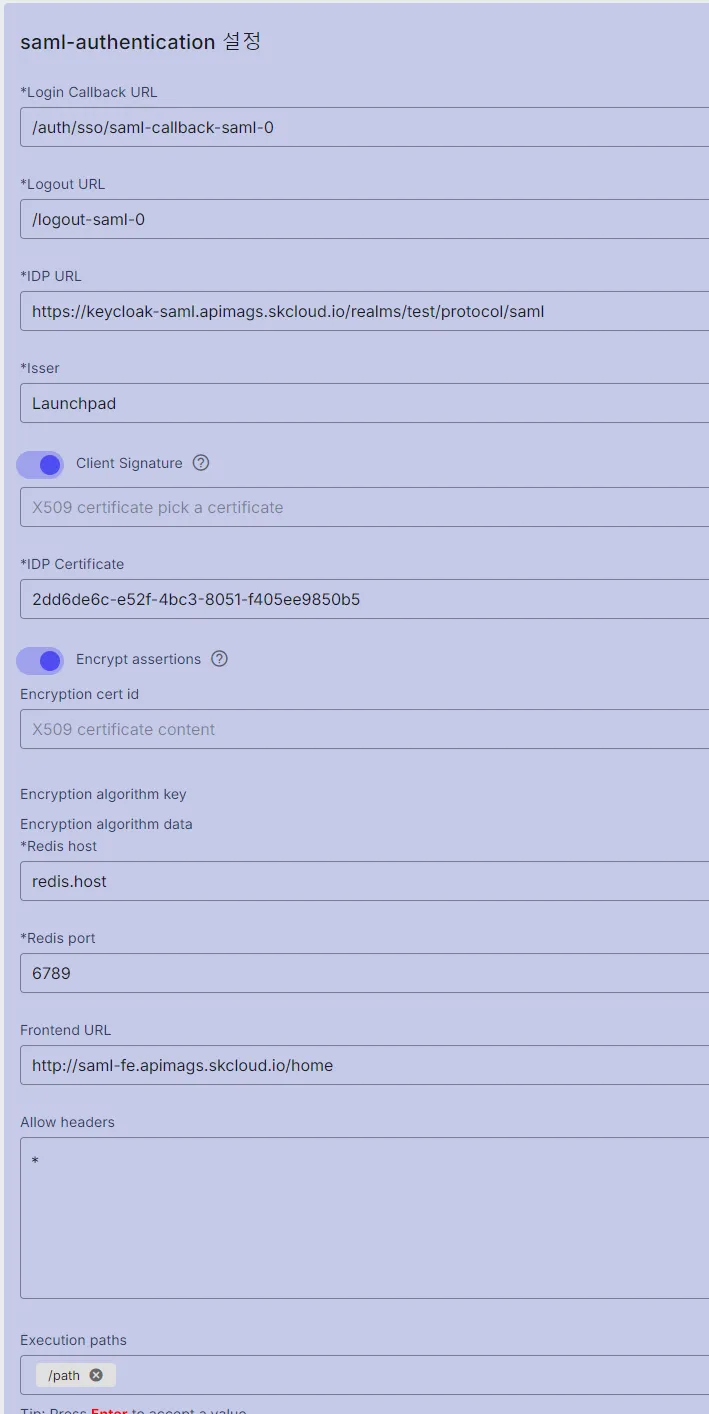
Configuration Details
| Field name | Description | Data input |
|---|---|---|
| Login Callback URL | Login Callback URL is the URL used to handle the response from the authentication server after the user has successfully logged in. The system redirects them back to the application at this URL to continue the process. | User-defined |
| Logout URL | When users make a logout request, the system will redirect to this URL to: - End the user session. - Delete the authentication session token or related session data. - Ensure that users are logged out of all services they had logged into. | User-defined |
| IDP URL | IDP URL (Identity Provider URL) is the URL of the identity provider in an authentication system. IDP URL is typically configured to: - Identify the address of the authentication server that users will use to log in. - Handle authentication requests and redirect users to the correct login page. | Step 1: Open keycloak. Step 2: Select the Realm. Step 3: Click the “Realm setting” in the left menu. Step 4: In the “Endpoints” field, click the link https://keycloak-saml.apimags.skcloud.io/realms/saml-test/protocol/saml/descriptor to be redirected to the document tree. Step 5: Get “Location” value of md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect. (See the NOTE below this table.) |
| Isser | Isser is: - A unique identifier for the identity provider. - Included in the authentication token or assertion to specify the authority that verifies the user’s identity. | Client ID of the Realm. |
| Client Signature | Client Signature is a digital signature created by the Client (customer or application). The Client Signature is often used to: - Verify that the request comes from a valid and trusted source. - Protect data from being altered or tampered with during transmission. - Ensure the authenticity of the Client when interacting with the Identity Provider (IdP) or other servers. This signature is typically created using the Client’s private key, then verified by the server with the corresponding public key to ensure validity. | Step 1: Obtain the Client Signature from this link: https://www.notion.so/Certificates-f0e62572160243ce800473766d1e7a08?pvs=4 Step 2: Export the Certificate form console Step 3: Open keycloak and select the Realm. Step 4: Click on “Clients” in the left menu. Step 5: Select the “Keys” tab. Step 6: Toggle “Client Signature Required” = ON to open the “Enable Client signature required?” Popup. Step 7: Import the file exported in the step 2. |
| IDP Certificate | IDP Certificate (Identity Provider Certificate) is a digital certificate issued by the Identity Provider (IdP) used to secure and authenticate during the authentication process between the IdP and applications or services. The IDP Certificate includes a public key that allows the receiving parties to verify the authenticity of messages from the IdP | Step 1: Open keycloak. Step 2: Select the Realm. Step 3: Click the “Realm setting” in the left menu. Step 4: In the “Endpoints” field, click the link https://keycloak-saml.apimags.skcloud.io/realms/saml-test/protocol/saml/descriptor to be redirected to the document tree. Step 5: Copy data in the ds:X509Certificate tag. Step 6: Paste the data obtained in step 5 into the IDP Certificate field. |
| Encryption cert id | The IdP uses the Encryption Cert ID to identify the correct encryption certificate when sending a message to the SP, ensuring the security of sensitive information during transmission. | Step 1: Obtain the Client Signature from the link: https://www.notion.so/Certificates-f0e62572160243ce800473766d1e7a08?pvs=4 Step 2: Export the Certificate form console Step 3: Open keycloak and select the Realm. Step 4: Click on “Clients” in the left menu. Step 5: Select the “Keys” tab. Step 6: Toggle “Encrypt assertions” = ON to open the “Enable Client signature required?” Popup. Step 7: Import the file exported in the step 2. |
| Redis host | Redis Host is the address of the Redis server that applications need to connect to for storing and retrieving data from the cache. | User-defined |
| Redis port | Redis Port is the network port that the Redis server uses to listen for and receive connections from clients. | User-defined |
| Frontend URL | This is the address that users use to open the application in a browser. | User-defined |
| Allow headers | Allow Headers are HTTP headers that the server permits the browser to use when sending requests to that server. | User-defined |
| Execution paths | A URL must contain this path for authentication to be applied. | User-defined |
Note:
- The textbox is only required if Client Signature is set to ON.
- The Encryption cert id textbox is only required if Encrypt assertions is set to ON.