Method for New TLS Configuration and Renewal for Gateway URL
This guide explains how to configure TLS for your API Gateway URL, covering certificate preparation, Kubernetes secret creation, and applying TLS through either the Kong Ingress Controller or APIM Console.
Initial TLS Setup (New)
First step is to prepare TLS Certificate and Key. To do this, you need two files:
- tls.crt: Public certificate file
- tls.key: Private key file
These can be issued by Let’s Encrypt or a private Certificate Authority (CA).
Registering TLS Certificate as a Kubernetes Secret
To use your TLS certificate in Kubernetes, you must register it as a secret in the namespace where Kong is installed (typically kong).
Command Line Example
kubectl create namespace kong # Skip if already created
kubectl create secret tls kong-gateway-cert \
--namespace kong \
--cert=certificate.crt \
--key=private.key
Parameter Description
| Parameter | Description |
|---|---|
| --cert | Path to the public certificate file |
| --key | Path to the private key file |
| --namespace | Namespace where Kong is installed (kong by default) |
Sample Secret (Raw YAML Format)
apiVersion: v1
kind: Secret
metadata:
name: kong-gateway-cert
namespace: kong
type: kubernetes.io/tls
data:
tls.crt: <base64 encoded certificate>
tls.key: <base64 encoded private key>
Applying TLS to Kong Gateway
Kong supports TLS configuration using:
- Ingress
- Gateway API
- KongIngress
This section explains both CLI-based and APIM Console-based methods.
Using Kong Ingress Controller (Default)
Define a TLS-enabled Ingress resource using the secret created earlier.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: kong-ingress
namespace: kong
annotations:
kubernetes.io/ingress.class: kong
spec:
tls:
- hosts:
- api.example.com
secretName: kong-gateway-cert
rules:
- host: api.example.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: kong-proxy
port:
number: 80
Important Notes:
| Point | Explanation |
|---|---|
| spec.tls.hosts | Define the DNS to be used (e.g., api.example.com) |
| spec.tls.secretName | Must match the secret name you created (kong-gateway-cert) |
| ingress.class | Must be kong (default when using Kong Ingress Controller) |
| backend.service.name | Typically kong-proxy if installed via Helm |
Using the APIM Console
You can also apply the certificate directly via the APIM Console. Navigate to APIM Console > Gateway Management > Gateway Detail Screen > Gateway URL Settings
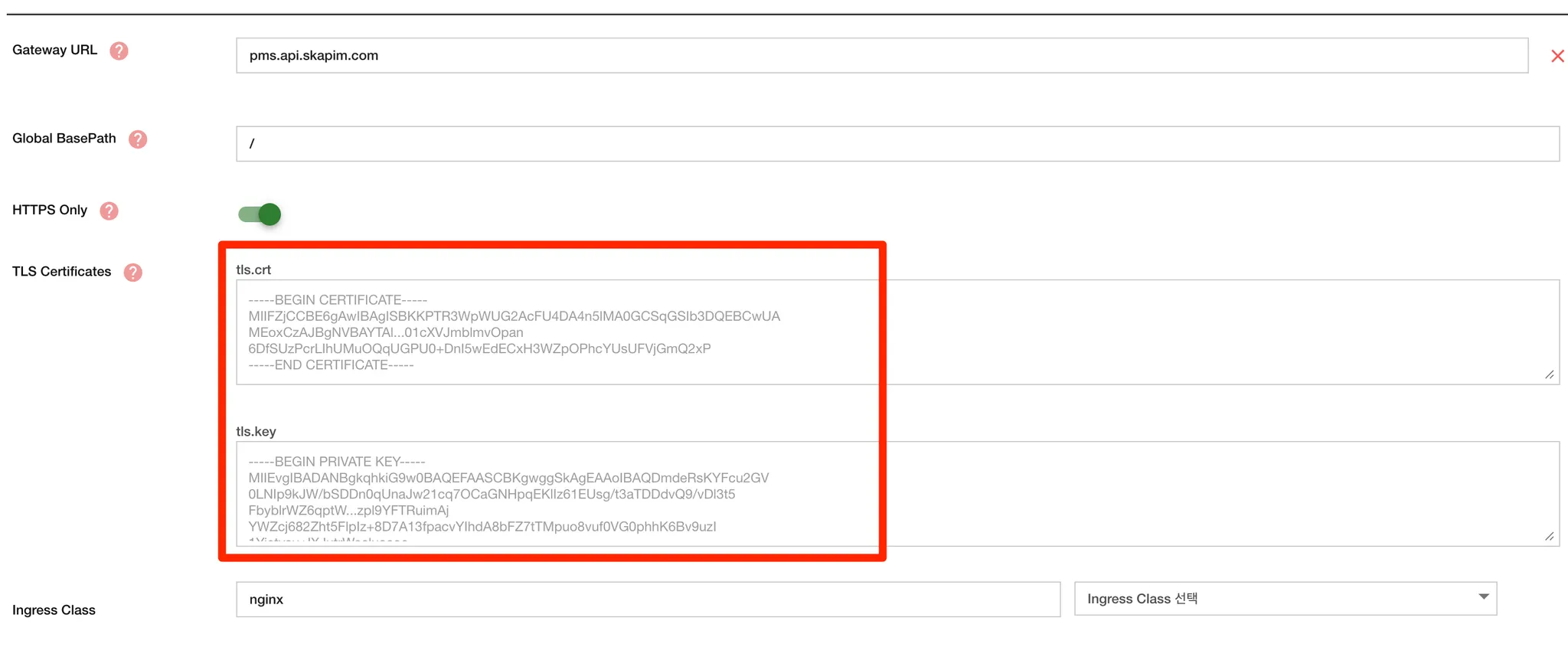
Input Fields:
- Gateway URL: e.g., pms.api.skapim.com
- Global BasePath: e.g., /
- HTTPS Only: Toggle ON
- TLS Certificates:
- tls.crt: Paste full certificate content
- tls.key: Paste full private key
- Ingress Class: Select appropriate class (e.g., nginx, kong)
Summary
| Step | Task |
|---|---|
| 1 | Obtain and prepare TLS cert (tls.crt, tls.key) |
| 2 | Create Kubernetes TLS Secret |
| 3 | Apply TLS via either Kong Ingress Controller or APIM Console |
| 4 | Confirm gateway access via HTTPS and matching DNS |
This guide ensures secure HTTPS routing for your API Gateway using TLS, whether managed by DevOps via CLI or via UI in the APIM Console.