Architectures
DEV/STG/PRD環境におけるAPIMデプロイメント
このアーキテクチャでは、APIMプラットフォームがKubernetesクラスターにデプロイされ、名前空間と役割によってセグメント化されています。このシステムは、開発、ステージング、プロダクションなどの複数の環境で独立して動作するように設計されています。
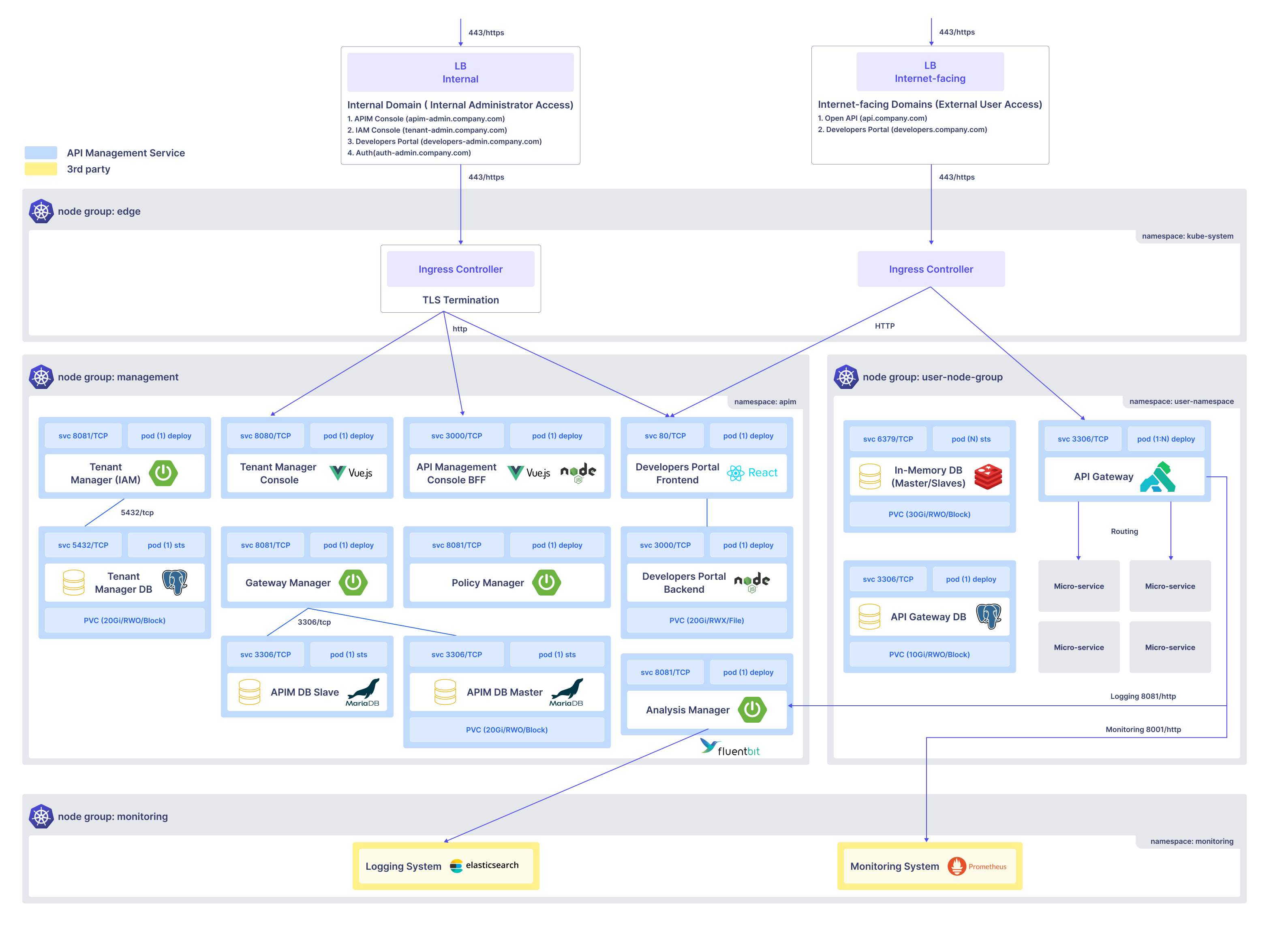
インフラストラクチャ層と外部/内部ルーティング
最上層では、システムは2つのロードバランサー(LB)を利用しています:
内部LB(管理者アクセス) - アクセスを提供します:
- APIMコンソール (apim-admin.company.com)
- IAMコンソール (tenant-admin.company.com)
- 管理者用開発者ポータル (developers-admin.company.com)
- 認証コンソール (auth-admin.company.com)
インターネット向けLB(ユーザーアクセス) - 外部アクセスを提供します:
- オープンAPIサービス (api.company.com)
- 公開開発者ポータル (developers.company.com)
トラフィックは、中央集権的なIngressコントローラーを通じてルーティングされ、TLS終端処理が行われ、ドメインパスに基づいて内部サービスにHTTPで転送されます。
ノードグループ:管理
このグループは、テナント、プロジェクト、ゲートウェイ、API、およびポリシーを管理するために必要なすべてのコアコンポーネントをホストします。
主要な名前空間:
namespace: apim
コアコンポーネント:
| コンポーネント | 説明 |
|---|---|
| テナントマネージャー (IAM) | システムユーザーとテナント組織のためのアイデンティティとアクセス管理を処理します |
| テナントマネージャーコンソール | テナント管理者用のUIフロントエンド(Vue.jsで構築) |
| API管理コンソールBFF | UIとサービスの相互作用を調整するバックエンド・フォー・フロントエンド(Vue.js & Node.js) |
| ゲートウェイマネージャー | ゲートウェイのプロビジョニングとプロジェクトとの関連付けを制御します |
| ポリシーマネージャー | IPフィルタリング、認証、ロギングなどのインバウンド/アウトバウンドポリシー定義を管理します |
| 開発者ポータル(フロントエンド&バックエンド) | APIユーザーが公開されたAPIをブラウズし、テストするためのインターフェース |
| 分析マネージャー | リアルタイムのAPI使用分析とレポートを処理します(FluentBitと接続) |
永続データベース:
- テナントマネージャーDB(PostgreSQL)
- APIM DB マスター/スレーブ(MariaDB)
- データの耐久性と冗長性のために構成されたPVC。
ノードグループ:ユーザーノードグループ
このグループは、ランタイムAPIトラフィックを実行し、ユーザーAPI呼び出しをバックエンドマイクロサービスにルーティングします。
名前空間:
namespace: user-namespace
コンポーネント:
| コンポーネント | 説明 |
|---|---|
| API Gateway | Kongベースのゲートウェイで、インバウンドAPIリクエストを処理します |
| API Gateway DB | ランタイムゲートウェイの設定と状態を保存するPostgreSQLストア |
| In-Memory DB (マスター/スレーブ) | トークン/セッションストレージに使用されます(おそらくRedisまたは類似のもの) |
| マイクロサービス | ルーティングされたAPIトラフィックを受け取る実際のバックエンドサービス |
API Gatewayは外部ユーザーからのリクエストを受け取り、以下を実行します:
- ポリシーの実行(認証、IPフィルタリングなど)
- 適切なマイクロサービスへのルーティング
- インバウンド経由でのレスポンスの返却
ノードグループ: モニタリング
| コンポーネント | 説明 |
|---|---|
| ロギングシステム | Elasticsearchによって提供され、構造化されたAPIログを収集するために使用されます |
| モニタリングシステム | Prometheusによって提供され、システムの健康状態とアラートのためのメトリクスを収集します |
ロギングおよびモニタリングコンポーネントはFluentBitおよびAPI Gatewayログと統合され、以下を可能にします:
- リアルタイムのAPIトラフィックの洞察
- カスタムメトリクスの視覚化
システム通信フロー
- 管理者はIngress Controllerを介して内部ドメインからシステムにアクセスします。
- ユーザーは外部ドメインを介してオープンAPIおよび開発者ポータルを呼び出し、Kong Gatewayにルーティングされます。
- KongはAPIポリシー(インバウンド/アウトバウンド)を強制し、各マイクロサービスにルーティングします。
- すべてのコンポーネントからのログとメトリクスは、モニタリングおよびロギングスタックにストリーミングされます。
クラウドおよびサードパーティサービスとの統合APIMデプロイメント
このアーキテクチャは、APIMシステムがAWSなどの外部インフラストラクチャおよびCloudWatch、Datadogなどのロギング/モニタリングサービスと統合される方法を示しています。
How It Works:- プライベートDNSまたはパブリックDNS(AWS Route53)は、APIMサービスが存在するKubernetesクラスターにリクエストを内部的にルーティングするために使用されます。
- リクエストがKong Gatewayに到達すると、インバウンドポリシーが適用され(認証、ヘッダーインジェクションなど)、トラフィックはバックエンドサービスにルーティングされます。
- レスポンスはアウトバウンドポリシー(例:データマスキング、ロギング)を通過し、クライアントに返されます。
- すべてのリクエスト/レスポンスログとメトリクスは、統合されたサードパーティのエクスポーターを介してCloudWatch、Datadog、またはWhatapに転送されます。
- Swaggerベースの仕様登録が使用され、Dev Portalを通じてAPIを動的に公開または更新します。
このアーキテクチャは、組織の境界を越えた安全でスケーラブル、かつ観測可能なAPI管理をサポートします。APIガバナンスを確保しつつ、クラウドネイティブサービスへのシームレスな拡張を可能にします。
開発環境の内部デプロイメント
このバージョンは、開発用のAPIMプラットフォームの内部専用セットアップを反映しています。APIテストやサービス開発中のセキュリティと閉じたアクセスを強調しています。
How It Works:- すべてのトラフィックは内部で流れ、プライベートDNSとALBを通じてクラスターに入ります。
- 内部開発者は、事前定義された内部サブドメインを介してAPIMコンソール、開発者ポータルにアクセスします。
- 開発フロントエンドアプリケーションからのAPIトラフィックはKong Gatewayに送信され、すべての設定されたポリシーが適用されます。
- バックエンドマイクロサービスは、ゲートウェイを通じてルーティングされたリクエストに応答します。
- 全体のスタックは、メンテナンス性と役割の分離のために名前空間で分離されています:
- apim は設定と制御ロジックを含みます。
- microservices はランタイムサービスとビジネスロジックを含みます。
このアーキテクチャは、公共ネットワークへの露出なしに安全なAPI開発とテストを可能にします。サービスの検証、ポリシーの適用、アクセス制御の確認に最適です。
開発専用内部フローモデル
このアーキテクチャは、ネットワークの境界と隔離に焦点を当てた開発環境内の詳細な内部トラフィックフローを示しています。
How It Works:- 内部アプリケーションと開発者は、プライベートドメインとNLB/ALBルーティングを通じてAPIMコンソールまたは開発者ポータルと対話します。
- フロントエンドからのリクエストはKong Gatewayにルーティングされ、そこで認証、レート制限、変換などのランタイムポリシーが適用されます。
- Gatewayは、同じクラスターにホストされているバックエンドマイクロサービスにリクエストをルーティングします。
- APIの使用状況、ログ、およびトラフィック統計は、Datadogのような内部の可観測性ツールに送信され、開発操作中の可視性を確保します。
- この環境には公開アクセスポイントはなく、API Gatewayを含むすべてのコンポーネントは厳密に内部です。
このセットアップは、APIの開発とテストのための安全で隔離されたパイプラインを確保し、完全な監視とガバナンス機能を保持します。これにより、開発チームは外部に露出することなく、プロダクションに似たAPIの動作をシミュレートできます。
コンポーネントの説明とリソース
この表は、APIMコントロールプレーン内の各コンポーネントに割り当てられたCPU、メモリ、およびストレージリソースを示しています。これは、インフラストラクチャおよびDevOpsチームがKubernetesクラスターを正確かつ効率的に計画およびプロビジョニングするのに役立ちます。
| Instance | Description | kind | Replicas | CPU (m) | CPU Total (m) | Memory (Mi) | Memory Total (Mi) | Storage (GB) | Storage Total (GB) |
|---|---|---|---|---|---|---|---|---|---|
| deploy-apim-analysis-manager | Analysis Manager | Deployment | 1 | 0.5 | 0.5 | 1024 | 1024 | 0 | 0 |
| deploy-apim-bff | APIM Console BFF | Deployment | 1 | 0.5 | 0.5 | 512 | 512 | 0 | 0 |
| deploy-apim-gateway-manager | Gateway Manager | Deployment | 1 | 0.5 | 0.5 | 768 | 768 | 0 | 0 |
| deploy-apim-tenant-manager | テナントマネージャー (IAM) | デプロイメント | 1 | 0.5 | 0.5 | 768 | 768 | 0 | 0 |
| deploy-apim-tenant-manager-console | テナントマネージャーコンソール | デプロイメント | 1 | 0.2 | 0.2 | 512 | 512 | 0 | 0 |
| deploy-apim-policy-manager | ポリシーマネージャー | デプロイメント | 1 | 0.2 | 0.2 | 512 | 512 | 0 | 0 |
| deploy-apim-developer-portal-backend | デベロッパーポータルバックエンド | デプロイメント | 1 | 0.2 | 0.2 | 512 | 512 | 20 | 20 |
| deploy-apim-developer-portal-frontend | デベロッパーポータルフロントエンド | デプロイメント | 1 | 0.2 | 0.2 | 64 | 64 | 0 | 0 |
| deploy-apim-mariadb-master | APIM DB (MariaDB マスター) | ステートフルセット | 1 | 0.5 | 0.5 | 512 | 512 | 10 | 10 |
| deploy-apim-mariadb-slave | APIM DB (MariaDB スレーブ) | ステートフルセット | 1 | 0.2 | 0.2 | 256 | 256 | 0 | 0 |
| statefulset-apim-tenant-manager-postgresql | IAM DB (PostgreSQL) | ステートフルセット | 1 | 0.5 | 0.5 | 256 | 256 | 10 | 10 |
| 合計 | 4 | 5760 | 40 |
- CPU: 4 コア
- メモリ: 6 GiB
- ストレージ: 40 GB
Notes:
- CPU/メモリはレプリカスケーリングポリシーに応じて増加します
- ロギング/モニタリングストレージはトラフィック量に応じてスケールします
- 1つのパブリックと1つのプライベートAPIMデプロイメントがサポートされています